Exam 1
Fall 2015
Paul Krzyzanowski
- 4 points
Why did the use of reference counting for remote objects prove to be impractical? Explain. - 4 points
(a) What is the advantage of vector clocks over Lamport clocks?
(b) What is a disadvantage? - 4 points
Attach Lamport time stamps to each of the following events. Assume that the initial clock value at each processor (before any event takes place) is 0.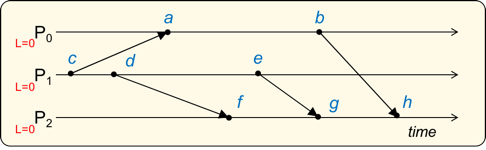
- 4 points
(a) Attach vector time stamps to each of the following events. Use a vector ordering of <P0, P1, P2> and assume that the initial clock value at each processor (before any event takes place) is 0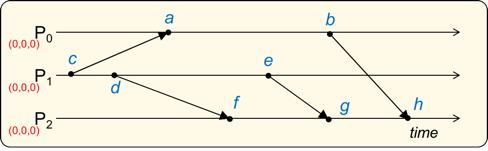
(b) Identify which event(s) is/are concurrent with event e. - Multiprocessor systems differ from a network of computers in that they:
(a) Are designed for high performance rather than high throughput.
(b) Must have a data communications network.
(c) Run specialized operating systems.
(d) Must have shared memory. - A Non-Uniform Memory Access (NUMA) system is called that because:
(a) A region of memory is local to each processor and can be accessed more quickly by that processor.
(b) Some memory may be located on remote computers and requires sending a request over a data network.
(c) Frequently-used memory is stored in a cache within the processor and can be accessed more quickly.
(d) Memory access time may vary depending on how much contention there is from other processors. - With home snoop caching:
(a) Each processor's cache always listens for memory operations on the bus and invalidates its cache if it sees writes for addresses it has cached.
(b) A CPU contacts the processor that is responsible for a specific memory address. That processor, in turn, forwards the request to the processor that has the latest cached value for that memory.
(c) Only one processor, called the home processor snoops on memory operations from all other processors.
(d) A CPU broadcasts a snoop request to all other processors, asking for the latest version of a memory address. - The end-to-end design principle states that:
(a) Network protocols should be implemented in layers to simplify programming and enable changes in protocols.
(b) Whenever possible, application-specific functions should be implemented at the end hosts of the network.
(c) The network should be smart enough to figure out how to deliver data from one endpoint to another.
(d) Every data packet should contain both the source address and destination address. - ONC RPC (the default RPC system on Linux, OS X, and BSD) does not support the following:
(a) Selection of transport protocol at run-time.
(b) Marshaling parameters to create a network message.
(c) Remote object references.
(d) A name server for service location. - Multi-canonical network data representation:
(a) Uses a textual representation for data to ensure maximum interoperability.
(b) Allows two processes to choose from one of several formats for representing data.
(c) Encodes the same data in both binary and text formats to simplify debugging and inspection.
(d) Encodes descriptive information about the data, such as names and types, in addition to the data. - Microsoft introduced the concept of a surrogate process to:
(a) Enable the client to locate the server.
(b) Create a proxy object that the client loads.
(c) Act as a secure gateway that validates all remote requests.
(d) Be the process that loads COM objects at the server based on client requests. - An RPC name server is used to:
(a) Obtain a unique name for a set of functions.
(b) Find the port number for a set of functions.
(c) Convert a function name to a remote address.
(d) Store distributed objects. - A key distinction between SOAP and REST interfaces is that:
(a) REST sends and receives documents while SOAP uses remote procedures.
(b) REST must use JSON to encode its data.
(c) REST is architecture independent.
(d) Operations are encoded in the document with SOAP but in the URL in REST. - Google Protocol Buffers are:
(a) A library for converting between different network protocols.
(b) An efficient binary method for serializing data.
(c) A library for buffering requests and responses to account for slow networks.
(d) A fast way to convert arbitrary data into portable text-based XML documents. - Java manages the lifetime of remote objects via:
(a) Tracking client connectivity.
(b) Leases.
(c) Remote reference counting.
(d) A distributed dependency graph. - Microsoft's Leasing Distributed Garbage Collector:
(a) Renews an objectÕs expiration timer whenever an object is accessed.
(b) Deletes replicas of an object when they are no longer referenced.
(c) Follows a chain of dependencies to clean up unused objects across multiple servers.
(d) Deletes an object only if its reference count is 0 and the object is not renewed. - Cristian's algorithm improves simply setting the clock to the value returned by the server by:
(a) Adjusting for drift.
(b) Adjusting for offset.
(c) Factoring in latency.
(d) All of the above. - A Berkeley clock master has a time of 1:20:00. Two slave systems, A and B, synchronize with the master. Currently, A has a time of 1:20:04 and B has a time of 1:20:05. After synchronizing, to what value does A set its clock?
(a) 1:20:00
(b) 1:20:02
(c) 1:20:03
(d) 1:20:04 - A stratum 2 NTP time server:
(a) Syncs from two servers for increased accuracy.
(b) Requires two network hops to connect to a client.
(c) Syncs its clock from a stratum 1 server.
(d) Is a backup for a stratum 1 time server. - PTP, the Precision Time Protocol:
(a) Assumes symmetric uplink & downlink delays.
(b) Requires the client to initiate the sync with the server.
(c) Measures, and accounts for, the differences between uplink and downlink latency.
(d) Is an extension to NTP with 128-bit precision for time values. - What can you tell by comparing two Lamport timestamps La and Lb? If La < Lb then:
(a) Event a must have happened before event b.
(b) Event a must have happened after event b.
(c) Events a and b are concurrent.
(d) None of the above. - A hold-back queue:
(a) Buffers received messages to deliver them at a constant rate to streaming media applications.
(b) Holds and re-sequences messages so they can be delivered in the correct order to applications.
(c) Holds messages at the receiver until an application is ready to consume them.
(d) Holds messages at the sender in case they need to be retransmitted due to network data loss. - A precedence vector enables:
(a) Global time ordering of messages.
(b) Total ordering of messages.
(c) Causal ordering of messages.
(d) Sync ordering of messages. - A rendezvous point in IP multicast is:
(a) A router in the network to which all sending hosts direct traffic that is addressed to specific multicast addresses.
(b) Each router that participates in forwarding multicast messages.
(c) A router on a LAN that accepts IGMP (Internet Group Management Protocol) messages
(d) A router that is responsible for managing the list of clients that subscribed to a specific multicast address. - Which mutual exclusion algorithm ensures that a process can be granted access to a resource in just two network messages assuming reliable message delivery and that no other processes are using the resource?
(a) Centralized.
(b) Token ring.
(c) LamportÕs.
(d) Ricart & Agrawala. - Which election algorithm does not always require contacting all group members?
(a) Bully algorithm.
(b) Ring algorithm.
(c) Chang and Roberts ring algorithm.
(d) All of the above require contacting all group members.
Part III – 14 points – 2 points each
- IP routers ensure that traffic is delivered reliably through the Internet
- TCP implements reliable communication on top of UDP, which is unreliable.
- Sockets are not needed for UDP communication since UDP is stateless.
- A problem with passing parameters by reference to a remote function is the lack of shared memory between the processes.
- Physical clocks must be synchronized on systems for logical clocks to work properly.
- Ricart & AgrawalaÕs mutual exclusion algorithm is more efficient than LamportÕs because it never requires comparing time stamps.
- If a network is partitioned (segmented), an election algorithm may elect multiple leaders.
Part I – 20 points
Part II – 66 points – 3 points each
For each statement, select the most appropriate answer.
For each statement, answer True (T) or False (F).