Malware
Malicious software and what to do about it
Paul Krzyzanowski
April 1, 2025
Malware
Malware refers to software that is intentionally designed to disrupt, damage, or gain unauthorized access to a computer system, network, or user data. It is typically installed without the user’s knowledge, often through deceptive or covert means.
Malware is commonly classified in two ways:
- By propagation method:
- How it spreads or is installed. This includes viruses, worms, trojan horses, and drive-by downloads.
By behavior or effect: What it does once installed. This includes spyware, adware, ransomware, wipers, and other forms of destructive or stealthy behavior.
For example, a piece of malware might propagate as a virus but act as ransomware once it is executed. These categories are not mutually exclusive, and we will define them in more detail shortly.
Some malware is designed to spy on users and collect sensitive data (spyware), while others bombard users with intrusive advertisements (adware). Some types encrypt the victim’s files and demand payment for recovery (ransomware), and others are designed to irreversibly erase data (wipers).
Malware can also be used to gain persistent remote control over a system. It may remain dormant until it receives instructions from a command-and-control (C&C) server, allowing it to operate as part of a larger botnet – a network of compromised machines that can be coordinated to launch distributed denial-of-service (DDoS) attacks or perform other large-scale malicious operations. In some cases, even seemingly legitimate software may contain a backdoor—a hidden mechanism that bypasses normal authentication or security controls to allow unauthorized access.
Malware Motivation
A principle often paraphrased from Sun Tzu’s The Art of War is: “Know your enemy.” In the context of malware, understanding an attacker’s motivation is key to anticipating threats and building defenses. Malware authors are driven by a variety of goals, some strategic and others opportunistic. We explored these motivations earlier in the course; below is a summary:
Stealing Account Credentials
Attackers often aim to capture login credentials. If a user’s username and password work on one system, there’s a good chance they’ll work on others due to password reuse. Credentials are valuable for identity theft, lateral movement, and unauthorized access.
Espionage
Rather than planting physical surveillance devices, modern attackers install spyware to monitor a target’s computer activity. This allows for the interception of emails, documents, keystrokes, and other sensitive data, often with greater reach than traditional methods.
Data Theft
Malware may be used to exfiltrate valuable data, such as trade secrets, research, or financial records. Some attacks are targeted at specific individuals or organizations; others are opportunistic, aiming to collect any monetizable data such as credit card numbers or personal identifiers.
Sabotage
Some attackers are motivated by revenge, ideology, or vandalism. Their goal is to damage or destroy data, systems, or reputations. Malware used for sabotage may delete files, corrupt systems, or render devices unusable.
Leveraging Compromised Systems
Attackers often compromise systems not to target the original user directly, but to extract value from the system itself—either by using it or by selling access to it.
Hosting illicit services: Malware can convert infected machines into infrastructure for underground operations. These systems may be used to send spam, mine cryptocurrency, host illegal content, or participate in a botnet used for DDoS attacks or credential stuffing.
Access-as-a-Service: In some cases, attackers act as initial access brokers, selling remote access to compromised systems—often via stolen credentials or malware implants—to other criminal groups. This reflects a modular malware economy, where different actors specialize in infection, persistence, monetization, and operations.
A botnet is a network of compromised systems controlled via a command-and-control (C&C) server, used either by the original attacker or rented out to others. Each of the machines in a botnet is referred to as a bot or zombie: they are given instructions on what actions to perform at a later time.
Advertising and Click Fraud
Some malware modifies browsers or system settings to show unwanted advertisements, redirect web traffic, or trigger fake ad clicks. This adware generates revenue for the attacker through fraudulent ad impressions and pay-per-click abuse.
Ransomware and Extortion
In ransomware attacks, files are encrypted and a ransom is demanded in exchange for a decryption key. Many modern variants also exfiltrate sensitive data, threatening to publish it unless the ransom is paid—a tactic known as double extortion. The rise of cryptocurrencies—especially those offering anonymity—has fueled a surge in ransomware, enabling attackers to collect untraceable payments. Ransomware is a form of reversible sabotage coupled with extortion.
Financial Fraud
Some malware directly supports fraud operations by enabling unauthorized financial transactions. This includes stealing payment card information, banking credentials, or initiating fraudulent transfers through infected endpoints. Stolen data may also be sold on underground markets for use in identity theft and other scams.
Hacktivism
Not all malware is deployed for profit. Some attackers are motivated by ideology or political agendas. These so-called hacktivists use malware to deface websites, disrupt communications, delete data, or leak sensitive information in support of a cause.
Another quote from The Art of War reminds us: “All warfare is based on deception.” This is especially relevant to malware, which is often installed through deception—such as tricking users into running it—rather than solely through the exploitation of software vulnerabilities. Understanding motivation helps explain the methods attackers use and reinforces the need for layered defenses.
Types of Malware
Worms and viruses
Worms and viruses are both types of malware designed to disrupt systems, steal data, or cause harm, but they differ in their behavior and methods of propagation.
Worms are self-replicating, standalone programs that spread automatically across networks or devices without requiring user interaction or a host file. Worms exploit vulnerabilities in operating systems, network services, or applications to gain access and propagate further. Once a worm is inside a system, it can scan for other vulnerable systems and replicate itself without further input. Because they act autonomously, worms can spread extremely rapidly and cause widespread disruption.
Viruses are malware that attach themselves to legitimate files or programs and rely on user interaction to spread. They infect executable files, boot sectors, or documents, and only propagate when the infected file or program is executed by the user. For instance, viruses such as Melissa and MyDoom spread through user actions like opening an infected email attachment. A virus might be sent as an email attachment that contains a document or software with the malware or a link to the malware. Unlike worms, viruses cannot spread independently; they need a host file to survive and a user to trigger their replication process.
A virus might even be a modification of the boot loader of a computer or the firmware on a flash drive. The key point is that it does not run as an independent process.
The distinction from a virus is that a worm runs as a standalone process while a virus requires a host program or file. A virus is executed because another program ran.
The popular use of both terms, worm and virus, has often blurred the distinctions between them. People often refer to any malware as a virus. Their malicious effects can be similar.
Components of Malware
Malware is often a structured system designed to infiltrate, persist, execute harmful actions, and avoid detection. Security analysts break down malware into functional components to better understand how it operates and how to defend against it.
The Classic Model: Three Core Components
In early analyses of malware, especially viruses, researchers typically described malware using three main components:
- Infection Mechanism
- The part of the malware responsible for spreading and gaining initial access. This might involve attaching itself to executable files (as in traditional viruses), exploiting a vulnerability (as in worms), or being bundled with legitimate-looking software. It is the initial step in delivering the malware to the target system.
- Payload
- The part of the malware that performs the actual malicious activity once the malware is active. Examples of payload functions include encrypting files (ransomware), logging keystrokes (keyloggers), exfiltrating files or credentials, and disabling security software. The payload is the primary “action” of the malware once it has infiltrated a system. In some cases, the payload may be a generic service that contacts a command and control server from which it gets specific instructions on what to do (e.g., mine cryptocurrency, send spam, participate in a DDoS attack) or a dropper that downloads the full payload (see below).
- Trigger
- The condition under which the payload is activated. Triggers can be: time-based (e.g., activating on a specific date), event-based (e.g., when a certain program runs or a command is received), or randomized or delayed to avoid detection.
The Modern Model: A Lifecycle-Based Framework
While the classic model worked well, it became useful to have more detailed breakdown of malware that reflects the full lifecycle of an attack. This model includes the following components:
- 1. Delivery (Initial Access)
- This is how the malware first enters the system (the infection mechanism in the classic model). Common delivery mechanisms include: phishing emails with malicious attachments or links, drive-by downloads_ from compromised or malicious websites, removable media_, such as infected USB drives, and exploits_ targeting vulnerabilities in exposed services or software.
- 2. Installation (Persistence Mechanism)
- After being delivered, the malware must establish itself on the system. This includes: writing files to disk or modifying legitimate applications, adding registry entries or system configuration changes to survive reboots, and installing persistence mechanisms such as startup scripts, services, scheduled tasks, or kernel-level components. Malware may also implement evasion techniques at this stage to avoid detection by antivirus or endpoint protection software.
3. Command and Control (C2) Many types of malware, especially those used in targeted attacks, need a communication channel to interact with an external attacker. The C2 component sends data (e.g., stolen credentials or files) to an attacker-controlled server and/or receives new instructions or updates. Malware may use HTTP(S), DNS, social media, peer-to-peer networks, or custom protocols to communicate stealthily.
4. Execution (Payload) Once the malware is installed and possibly under the control of the attacker, the core malicious behavior—the payload—is executed. Common payloads include: data theft or spying (keylogging, screen capturing), file encryption and ransom demands, system disruption or sabotage, and lateral movement to other systems in the network. In traditional malware, the payload may be embedded in the original code; in more modular or stealthy variants, it may be downloaded after initial access.
- 5. Evasion and Trigger
- To avoid being caught, malware often includes sophisticated evasion mechanisms, which can include:
- Code obfuscation, compression, or encryption to hide its true behavior
- Rootkits to hide files, processes, or network activity
- Environment checks to detect if it’s running in a sandbox or VM
- Polymorphism or metamorphism to change its appearance over time
- Triggers determine when the malware activates. Some lie dormant for weeks to avoid detection while others respond only to specific C2 commands. Many variants delay execution until specific conditions are met (e.g., running on a certain system or with admin privileges).
Droppers and Packers
A dropper is a special type of malware that doesn’t contain the main payload itself but is designed to install it. It often acts as a first-stage malware, whose sole job is to establish a foothold on the system, perform initial evasion (e.g., disabling antivirus), and then download or unpack the actual malware payload. Think of it as a bootloader for malware.
A packer is a tool used to compress or obfuscate malware, making it harder to detect or analyze. It disguises the malware’s code to bypass antivirus detection or complicate reverse engineering efforts. Packers are commonly used by attackers to evade traditional signature-based detection methods. For instance, a packer might encrypt the malware’s code and only decrypt it during runtime to execute the attack.
Summary Table: Modern Malware Components
| Component | Description | Example Techniques |
|---|---|---|
| Delivery | Entry into the system | Phishing, exploits, USB, drive-by download |
| Installation | Persisting on the system and surviving reboots | Registry edits, startup tasks, services |
| Command & Control | Communication with attacker or server | Encrypted HTTP, DNS tunneling, Tor |
| Execution | Execution of malicious actions | Data theft, ransomware, keystroke logging |
| Evasion & Trigger | Obfuscation, anti-analysis, and conditions for activation | Sandbox detection, delayed execution |
| Dropper | Installs or fetches main malware payload | Downloader script, embedded archive |
| Packer | Obfuscates the malware | Encryption, compression, code modification |
Malware Infiltration: Delivery Mechanisms
Malware does not appear on a system by magic—it must get there through some form of delivery. These delivery mechanisms vary widely, from user mistakes to automated exploitation. Understanding the different ways malware can enter a system helps us design better defenses. These are the primary vectors of initial access:
1. User-Initiated Installation
In many cases, users inadvertently install malware themselves. This can occur through compromised trusted software, deception, or even ordinary workplace activities.
Supply Chain Attacks
Attackers may infiltrate software at its source. In a supply chain attack, legitimate software includes malicious components, often introduced through compromised build systems, third-party libraries, or tampered installers. Once users install the software, the malware is quietly delivered along with it.
Examples:
- SolarWinds Orion (malicious update in a trusted IT monitoring tool)
- CCleaner (legitimate tool compromised during development)
Social Engineering
Social engineering attacks exploit human psychology—trust, curiosity, urgency, or desire for free software—to trick users into installing malware. Social engineering attacks include deceptive downloads, phishing, and business process abuse.
Deceptive Downloads
Users are misled into installing malicious software that appears legitimate or beneficial. This includes:
- Fake utilities (e.g., “System Optimizer”, “PC Cleaner”)
- Fake updates or installers (e.g., bogus browser updates)
- Cracked software or license key generators
- Malicious mobile apps posing as helpful tools or games, especially prevalent in third-party app stores. These apps may exfiltrate data, run in the background, or download additional payloads.
Phishing Attacks
Phishing emails attempt to trick recipients into clicking on malicious links or opening attachments. These messages often appear to come from trusted organizations and include plausible requests (e.g., “your account was compromised”).
More advanced than generic phishing, spear phishing targets a specific individual or organization. These messages are highly tailored, using personal information or organizational context to increase credibility.
Business Process Abuse
Attackers can exploit routine workflows. For example:
- Documents or spreadsheets with embedded macros that execute malicious scripts when opened.
- Shared files sent by email or uploaded to collaborative platforms that exploit client-side vulnerabilities.
2. Removable Media Infections
Malware can also enter a system through infected USB drives or other removable media. These attacks remain common in both corporate and air-gapped environments.
- Malicious firmware on USB devices can exploit low-level drivers.
- Infected installers or files on removable drives trick users into launching malicious software.
- Some malware is triggered automatically when the device is accessed or browsed, especially on systems with poor USB handling or autoplay enabled.
3. Software Vulnerability Exploits
Malware may be delivered by exploiting vulnerabilities in software running on the system. These attacks often require no user interaction and may target:
- Command injection
- Code injection
- SQL injection
- Remote code execution (RCE)
- Authentication bypass or backdoors
These vulnerabilities can be exploited via network services, exposed APIs, local software, or third-party applications.
4. Web-Based Attacks and Zero-Click Exploits
The web is a frequent malware delivery channel, capable of infecting systems without downloading traditional files.
Drive-by Downloads
A drive-by download occurs when visiting a compromised or malicious website triggers a download or execution of malware without explicit user approval. This typically involves:
- Exploit kits probing the browser or plugins,
- Vulnerabilities in Flash, Java, PDF readers, or outdated browsers,
- Weak sandboxing or misconfigured security settings.
The user may not need to click anything – merely loading the page is enough.
Zero-Click Exploits
Zero-click exploits are more sophisticated: no user interaction is needed at all, not even visiting a website. These attacks exploit vulnerabilities in the software that automatically processes content, such as:
- Messaging apps (e.g., iMessage, WhatsApp),
- Email clients,
- Image or document parsers.
For example, a malicious image or SMS may trigger an exploit just by being received. Zero-click exploits are rare, costly to develop, and typically used in targeted surveillance or espionage operations.
Summary: Common Malware Delivery Vectors
| Vector | Requires User Action? | Common Targets | Example |
|---|---|---|---|
| Supply Chain Attack | No | Any system | SolarWinds |
| Deceptive Download | Yes | End users | Fake browser update, cracked software |
| Phishing | Yes | Email recipients | Invoice with malware attachment |
| Spear Phishing | Yes | Specific individuals | HR director receives fake job application |
| Malicious App | Yes | Mobile devices | Fake flashlight app on third-party store |
| Macro Document | Yes | Office environments | Excel sheet with macro to download payload |
| Infected USB Device | Yes (or sometimes no) | Air-gapped or sensitive systems | Plugged-in USB with autorun malware |
| Remote Exploit (Zero/N-day) | No | Servers, clients, any endpoint | Exploit for unpatched RDP vulnerability |
| Drive-by Download | Sometimes | Web browsers and plugins | Exploit kit on a compromised website |
| Zero-click Exploit | No | Messaging/email/media apps | Malicious SMS triggering remote code execution |
Zero-day and N-day exploits
Attackers often exploit software vulnerabilities—especially in network-facing services—to inject code or commands that download and execute malware.
A particularly valuable class of vulnerabilities for attackers are zero-day vulnerabilities. These are software bugs that are unknown to the vendor and the public at the time of their discovery. Because no patch exists, they are unmitigated and highly effective for initial compromise. The term zero-day reflects the fact that developers and administrators have had zero days to respond with a fix once the vulnerability becomes public.
Until a patch is released, an attacker can assume that the exploit will succeed on most systems running the vulnerable software, regardless of how up-to-date or well-maintained those systems otherwise are.
A related concept is the N-day vulnerability. These are publicly known vulnerabilities for which a patch or mitigation already exists. Once a vulnerability is disclosed, software vendors may release a fix, and IT teams can take action, such as applying patches, disabling services, or enabling detection mechanisms. However, these defenses are not applied universally or immediately. The time window between the disclosure of a vulnerability and the widespread deployment of a fix is referred to as the N-day window. During this period, attackers can still exploit unpatched systems.
Zero-day vulnerabilities may initially be exploited by only a small number of attackers, or not at all. However, once a patch is released, researchers and adversaries alike can examine the code changes to identify what was fixed. This process, known as patch diffing, can reveal the nature of the vulnerability, enabling the creation of new exploits. In this way, a zero-day vulnerability often transitions into an N-day vulnerability—one now available to a broader set of attackers.
This dynamic creates a race: attackers attempt to reverse-engineer patches and launch exploits faster than defenders can apply updates. Ironically, releasing a patch can temporarily increase the risk of exploitation, as it draws attention to the vulnerability in unpatched systems.
Example: Lifecycle of a Zero-Day → N-Day Exploit: EternalBlue
Discovery Private Use Public Disclosure Patch Released Widespread Exploitation
│ │ │ │ │
▼ ▼ ▼ ▼ ▼
[0] ────●───────────────●───────────────┬──────────────●───────────────┬───────────────▶ Time
│ │
Zero-day exploit N-day exploit window
(private use) (unpatched systems at risk)
Vulnerability: CVE-2017–0144 (SMBv1 in Microsoft Windows)
- Zero-day Phase: Discovered and weaponized by the NSA as part of their cyber arsenal. The vulnerability was unknown to Microsoft or the public.
- Leak: In April 2017, the hacking group Shadow Brokers leaked the NSA’s exploit, named EternalBlue.
- Patch Release: Microsoft had already released a patch (MS17–010) in March 2017, likely informed through classified channels.
- N-day Exploitation: After the leak, attackers reverse-engineered the patch and launched massive attacks on unpatched systems.
- Notable Attacks:
- WannaCry ransomware (May 2017)
- NotPetya pseudo-ransomware (June 2017)
Despite a patch being available, many systems remained unpatched, illustrating the long and dangerous N-day window.
Infiltration: A Deeper Dive
We’ve covered an overview of the ways that malware can enter systems. In these next few sections, we’ll explore a few topics in greater depth.
Older Connected Devices (Internet of Things)
While most people keep their PCs up to date with the latest security patches, the same cannot be said for other internet-connected devices, which can include routers, printers, kitchen appliances, security cameras, industrial control equipment, and many other devices.
These devices often lack necessary updates and security features, making them prime targets for cyber attackers. They be often be easily exploited and added to botnets—a network of compromised devices used to execute malicious activities such as DDoS attacks and data theft.
One example (November 2024) of a threat actor exploiting these vulnerabilities is Volt Typhoon, a state-sponsored hacking group linked to China. Known for its sophisticated and stealthy operations, Volt Typhoon focuses on cyber espionage and targets critical infrastructure in the United States. The group uses a tactic known as “living off the land” (LotL), relying on legitimate administrative tools already present in systems to avoid detection. By compromising outdated devices, Volt Typhoon can build large botnets without leaving obvious traces, enabling them to disrupt communication channels, access sensitive information, and execute large-scale attacks.
Manufacturers of devices stop support at a certain time: it simply does not make economic sense to maintain software for older devices even if they are still in widespread use. In November 2024, for example, D-Link announced that it no longer supports over 60,000 deployed network-attached storage devices even though they are vulnerable to a command injection vulnerability with a published exploit that allows an attacker to send HTTP GET messages to run arbutrary shell commands on these devices. With access to the network, an attacker can simply run a curl command to target the device:
curl "http://[Target-IP]/cgi-bin/account_mgr.cgi cmd=cgi_user_add&name=%27;<INJECTED_SHELL_COMMAND>;%27"
Social engineering
By far the most common way that malware enters a system is via deception: the legitimate user of the system installed it unknowingly. This uses a social engineering attack to convince the user that it is in his or her interest to install the software.
Social engineering is the art of manipulating, influencing, or deceiving a user into taking some action that is not in his/her or the organization’s best interest. The goal of social engineers is to obtain your trust and get you to divulge information or provide them with some form of access. In computers, social engineering refers to any techniques used by an adversary to trick you into disclosing information, opening an attachment, downloading a file, reading a message, clicking on a link, installing a program, or running a command.
For example, the May 2024 cyberattack on the Ascension healthcare facilities in the U.S. began when an employee downloaded a malicious file they thought was legitimate. It led to the installation of ransomware and propagation to multiple servers, impacting pharmacies and hospitals across. 19 states.
Websites may offer downloads of “security” software, system “cleaner” software, or software “updates,” none of which will do their purported task. An attacker may convince a user to click on a URL in an email attachment or a web page. Software obtained from file sharing services are also excellent venues for distributing malware. A user may try to avoid spending $4,000 for an AutoCAD license or $240/year for an Adobe Illustrator license and turn to a file sharing site to download a patched copy or a crack for the software that bypasses license checks. Quite often, these downloads contain malware instead of the desired software (what do you expect – the user is acting as a thief by downloading software from thieves).
Downloads can also be initiated by tricking users into thinking they’re dismissing an error or downloading something innocuous. For instance, attackers have been found to use JavaScript to overlay fake error messages from Google Chrome, Microsoft Word, and Microsoft OneDrive. These “errors” direct the user to copy a PowerShell fix. Into a clipboard and then run it.
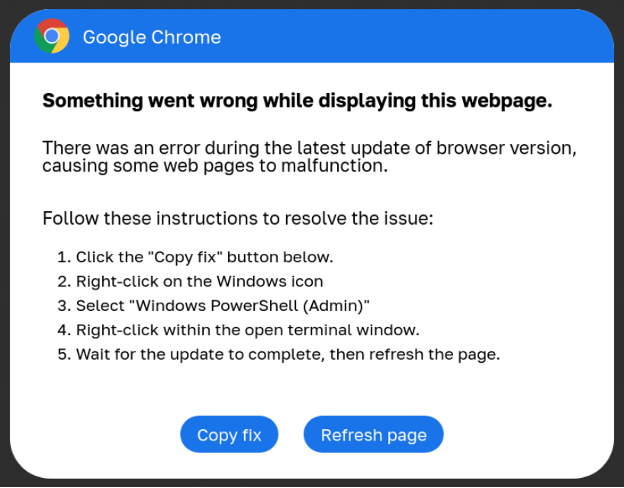
Attackers have also emailed HTML attachments that look like Microsoft Word Documents that, when opened, present a prompt asking the user to install a “Word Online” extension to be able to view the document. The download is, of course, not an extension and directs users to run the attacker’s script. The unsuspecting user believes they’re installing a legitimate Microsoft extension.
Any information the attacker can get about a user can help an attacker create a more convincing social attack. The term pretexting refers to using a concocted scenario to contact a user and get additional information (e.g., an attacker can pretend to be a caller from the IT department or a high-level manager from another location to try to extract information; with some rudimentary information, the attacker can mention some employee, department, or project names to sound like a true insider).
Luring developers – 2024
Social engineering may involve winning someone’s trust by appearing to be helpful. Offering security updates is a form of that. A more direct example surfaced in mid 2024 where a user on Stack Overflow offered to “help” developers on Stack Overflow by telling them to install the pytoileur package, which purports to be an API management tool written in Python. If someone inspects the code, it will look innocent unless they notice that there’s a lot of whitespace with the code appearing far to the right, requiring horizontal scrolling and will likely be unnoticed by the victim.
The package targets Windows systems and downloads a malicious program called Runtime.exe that is then run via the Windows PowerShell and VBScript commands. The package also installs additional executables and modifies registry settings. One of these packages tries to upload user profiles from browsers and crypto services.
Dev Popper – 2024
As an example of a novel but uncommon type of social engineering, a malware campaign called Dev Popper was documented in April 2024 that targeted software developers with fake interviews and got them to install a remote access trojan, which would allow intruders future access to their computers. This is a social engineering attack where the victims believed they were participating in a job interview. They willingly downloaded a zip file in order to demonstrate that they can download and run code from Github. Note that, although the software is described as a trojan, it’s not clear that it presented any useful purpose but did have the property that the user installed it willingly.
QR Code Scams
QR Code Scams and Social Engineering
QR code scams, sometimes called quishing, have become a growing social engineering threat, especially in urban areas where mobile payments are common. These scams take advantage of users’ trust in quick-response (QR) codes, which are widely used to simplify actions like paying for parking, accessing websites, or downloading apps. The attack works by placing a malicious QR code over a legitimate one, often on parking meters or public kiosks. When scanned, the fake code leads to a phishing site or payment portal controlled by the attacker.
The scam is effective because users are conditioned to trust and act on QR codes without much scrutiny. Unlike a suspicious-looking email or URL, a QR code doesn’t visibly expose where it’s sending you. Victims are typically redirected to a spoofed site that looks like a legitimate parking payment page. Once there, they might unknowingly enter credit card details, mobile payment credentials, or download a malicious app. Some versions of the scam even trigger automatic downloads of malware, especially on devices with lax security settings.
Recent incidents illustrate the scale of the problem. In Orlando, city officials found over 200 fake QR codes pasted onto parking meters downtown, fooling drivers into paying fraudsters instead of the city. In New York City, scammers have placed deceptive QR stickers on meters to intercept payments. Similar scams have been reported in Birmingham, Alabama, and across the UK, where attackers used well-crafted phishing pages to steal card data from drivers. In many cases, victims only discover the fraud when they get parking tickets for unpaid meters or notice unauthorized transactions on their bank accounts.
QR scams show how low-tech tactics can still bypass security measures by exploiting human behavior. The success of these scams depends less on technical sophistication and more on convincing design and opportunistic placement. They blend phishing with physical tampering, making them harder to detect than purely online attacks.
Some references if you’d like to read about the QR scams:
- WBRC, “Scammers using fake QR codes to steal from people paying for parking,” May 31, 2025. https://www.wbrc.com/2025/05/31/scammers-using-fake-qr-codes-steal-people-paying-parking/
- Gothamist, “Parking in NYC is hard enough. Don’t get suckered by the meter,” May 28, 2025. https://gothamist.com/news/parking-in-nyc-is-hard-enough-dont-get-suckered-by-the-meter
- FOX 35 Orlando, “Orlando parking meter scam: 200 fake QR codes found downtown,” May 23, 2025. https://www.fox35orlando.com/news/orlando-parking-meter-scam-200-fake-qr-codes-found-downtown
- The Guardian, “QR code scam: what is ‘quishing’? Drivers targeted in fake parking payment fraud,” May 25, 2025. https://www.theguardian.com/money/2025/may/25/qr-code-scam-what-is-quishing-drivers-app-phone-parking-payment
Supply Chain Attacks in Distributing Malware
Supply chain attacks exploit vulnerabilities in the production, distribution, or deployment of software or hardware by compromising a trusted third-party component. Attackers target dependencies to inject malicious code, which is then propagated through the supply chain, allowing malware to be distributed through widely trusted channels. These attacks are particularly dangerous as they undermine trust in legitimate software, potentially impacting thousands or millions of users.
We’ll examine a few common types of supply chain attacks in software distribution, including typosquatting, infected development tools, and malicious packages.
Typosquatting
Typosquatting involves creating malicious software packages with names similar to legitimate packages, hoping that developers will accidentally download and use the harmful version due to a minor typo in the name. This attack leverages human error to infiltrate systems by mimicking legitimate dependencies.
An example of typosquatting occurred when malicious packages were uploaded to the Python Package Index (PyPI) under names similar to popular packages. Attackers exploited minor misspellings or alternative naming conventions, causing unsuspecting developers to download and install these malicious packages, which often contained data exfiltration or credential-stealing code (DataBreachToday, 2024).
XcodeGhost
XcodeGhost is an example of an attack targeting a development tool. In this case, a modified version of Apple’s Xcode development environment was distributed through third-party websites. XcodeGhost included malicious code that was injected into any app compiled with the infected version of Xcode, allowing it to compromise applications distributed via Apple’s App Store. The malware gathered device information, including the app’s bundle identifier, network information, and other sensitive data, and sent it to the attacker’s server.
Developers in regions with slower internet connections sometimes downloaded Xcode from unofficial sources, unknowingly downloading XcodeGhost instead of the legitimate package. Once an app was compiled with this infected version of Xcode, it was virtually impossible for developers or users to detect that it contained malware (Wikipedia, 2024).
Malicious Packages Repositories
Repositories for open-source software packages, such as GitHub and PyPI, are frequent targets of malicious actors. Attackers upload packages that contain malware, either by creating new, seemingly useful packages or by compromising existing packages. When developers include these packages in their projects, they unknowingly introduce malware.
GitHub and Other DevOps Platforms: Malicious actors exploit platforms like GitHub by uploading harmful repositories or modifying dependencies in existing projects. Attackers may hijack inactive or poorly maintained repositories, injecting malicious code that is automatically pulled in by any projects relying on these dependencies (SentinelOne, 2024).
Malicious Python Packages on PyPI: The Python Package Index (PyPI) has seen numerous instances of malicious packages that exfiltrate credentials. For example, a recent malicious package was found to exfiltrate AWS credentials when installed. Attackers exploited developers’ reliance on PyPI, which often handles trusted packages, to insert malware and gain unauthorized access to sensitive cloud environments (Fortinet, 2024).
These malicious packages are especially dangerous because they directly attack software that developers trust and frequently rely on. Once a developer incorporates a malicious package, it often goes undetected until the malware is triggered, allowing attackers to access confidential information, disrupt services, or compromise data integrity.
Supply chain attacks are an increasingly prevalent threat. Defending against these attacks requires careful verification of package authenticity, vigilance in downloading tools from official sources, and consistent monitoring of dependencies.
Credential stuffing
An attacker may obtain collections of stolen email addresses (or usernames) and passwords. Since people often use the same name and password on multiple systems, this often give the attacker access to services on other websites on which the user has accounts. Accounts for banking sites are, of course, particularly valuable since they can be a direct conduit for transferring money. This attack is called credential stuffing.
In some situations, such as getting access to a user’s email accounts, an attacker can log onto the systems or services as the owner of the account and install malware, monitor the internal organization, and even send email, disguised as the user (e.g., contact other employees or friends), which becomes a powerful social engineering attack.
Malware residence: where does it live?
File infector virus
A file infector virus is a virus that attaches itself to an executable program. The virus patches the program so that, upon running, control will flow to the the virus code. Ideally, the code will install itself in some unused area of the file so that the file length will remain unchanged. A comparison of file sizes with the same programs on other systems will not reveal anything suspicious. When the virus runs, it will run the infector to decide whether to install itself on other files. The trigger will then decide whether the payload should be executed. If not, the program will appear to run normally.
Bootloader malware
Bootkits, also known as boot sector viruses, are malware that targets the booting process of a system. The malware has an infector that installs itself in the Master Boot Record (MBR) of a disk. In older BIOS-based PC systems, the first sector of the bootable storage device is read into memory and executed when the system boots, Normally, the code that is loaded is the boot loader that then loads the operating system. By infecting the master boot record, the virus can repeatedly re-infiltrate the operating system or files on the disk even if any malware on the system was previously detected and removed.
Boot sector viruses were common in the early days of PCs when users often booted off floppy disks and shared these disks. The virus would often use DOS commands to install itself onto other disks that it detects. Users on those systems had full administrative rights to modify any part of the system.
These viruses have diminished as attackers found more appealing targets. However, attacks on the bootloader are a continued threat. 2011 saw the emergence of ransomware that modified the boot loader to prevent the operating system from booting unless a ransom was paid. In 2016, Petya Trojan ransomware was deployed, which also infects the MBR and encrypts disk contents.
Infected removable media, flash drives
In the early days of PCs, people would share content by passing around floppy disks. At the time, this became a means for viruses to spread, which could be planted in either the boot sector or in files. Today, people often share USB flash drives the way they used to share floppies.
Autorun
In earlier Windows systems, Microsoft provided a feature called AutoRun.
It was designed to make the CD (and, later, DVD and flash drive) experience better for users, particularly when using CDs for software installation. If the CD contained a file called autorun.inf, Windows would automatically execute a program identified within that file. While this made the experience of figuring out what to do after a CD is inserted easier for most users, it created a horrific security vulnerability: all that an adversary had to do was to get you to insert the media. Moreover, this functionality worked with any removable storage so that inserting a flash drive would automatically run a program defined
within autorun.inf on the drive.
Microsoft eventually removed this capability from flash drives but then some manufacturers created USB drives that emulated a CD drive to offer the “convenience” of AutoRun. Microsoft ultimately removed this functionality altogether in Windows 7.
USB Firmware
The more insidious problem with USB flash drives now is unprotected firmware. USB flash drives aren’t just dumb storage: they include firmware – embedded software on the chip. The firmware runs when you plug the drive into your computer, identifying the drive as a USB storage device and managing the transfer of data. You don’t see this firmware and cannot tell if it has been changed.
Because the firmware defines the USB device, modified firmware on the flash drive could present the drive as a keyboard and send a set of keyboard commands to the host system (for example, commands to open the terminal window and delete files).
A USB device can have multiple profiles associated with it and thus present itself as multiple devices, so the flash drive can tell the computer it is a keyboard but also a flash drive, so the user will still be able to use the device as a storage device. The firmware could also modify file contents as they pass between the USB storage device and host computer. The same attack can be user on other USB devices. For example, an ethernet adapter can redirect network messages to an attacker’s site.
Reprogramming the firmware has not been exploited by malware thus far, at least not in a widespread manner, but the vulnerability has been demonstrated and the source is freely available. BadUSB is a proof-of-concept attack that reprograms a USB drive’s controller to behave as a Human Interface Device (HID), such as a keyboard. Once plugged in, it can type commands, download malware, create users, or reconfigure the system—all without user consent.
Data leakage
The most common problem with flash drives is their portability and small size: they are easy to lose and easy to borrow. This makes them vulnerable to data leakage, which is just a fancy term that means some adversary may access your data simply by borrowing your flash drive.
In 2016, researchers at the University of Illinois ran an experiment where they scattered nearly 300 USB drives in public areas through the campus. Each of those drives was loaded with files that, when opened on a network-connected computer, would contact a server to tell it that the drive has been picked up and the file was opened. The results of the study showed that 98% of the drives were picked up and someone opened up at least one file on 45% of them1. Because of the risk of malicious firmware, even formatting a drive does not make it safe to use.
Inadvertent program execution
The portability of flash drives makes them a distribution mechanism. Experiments of scattering a number of them in parking lots revealed that many people are all too willing to plug a random drive into their system.
Even without automatic execution capabilities enabled, attackers can use flash drives as a distribution mechanism for malware. The Stuxnet attack on Iranian centrifuges exploited a Windows bug in rendering shortcut icons, where just viewing them in Windows Explorer enabled the execution of arbitrary code. Others have exploited a bug in video playback that allowed code execution. Even something as simple as an HTML file on a drive may direct the target to a website that can launch an attack.
There are many other USB device-based attacks. Take a look here if you’re curious.
Macro viruses
Some applications have support for macros, which allow the user to define a set of commands to avoid repetitive tasks and improve productivity. They are particularly common in text editors but are present in other applications as well, such as Photoshop and Microsoft Word and Excel. In some cases, as with Microsoft Office applications, macros are embedded in the document, which means they can be passed on to other users who access that document. Some macro capabilities are far more powerful than simply defining repetitive commands. Microsoft Office products, for example, provide Visual Basic scripting, which effectively allows users to embed complete programs into their documents. VBScript is based on Visual Basic and provides features that make it easy to access network printers, network files, special folders, user information, and even execute scripts on remote systems.
Scripts in Office documents can spread not only by having the user pass the original infected
document around but by modifying the
default template file, normal.dot. This will affect every
other document on the system.
With operating systems providing better access controls and users not running with administrative privileges, embedded scripts are a ripe area for attack. If you can
convince somebody to open a document, they will run your program on their
machine.
The challenge, of course, is to get a file with a malicious macro to target users and get them to open it. One of the most common techniques is to send it as an email attachment with some inducement to get the user to click on the document. This is an example of social engineering.
One hugely-successful virus that did this
was the ILOVEYOU virus from 2000. The subject of the message stated that
it is a letter from a secret admirer. The attachment wasn’t even a document;
it was a visual basic script. To provide a better user experience, Microsoft
would hide file extensions by default (macOS does this too). The file was
named LOVE-LETTER-FOR-YOU.TXT.vbs but the .vbs suffix, which
indicated that the file was a visual basic script, was hidden from users, so
they only saw LOVE-LETTER-FOR-YOU.TXT. Not being aware of when extensions
are hidden and when they are not, millions of users assumed they received
an innocuous text file and clicked on it. Upon execution, the script would
copy itself into various folders, modify and add new entries to the system registry,
replace various types of files with copies of itself (targeting music and
video files), and try to propagate itself through Internet relay Chat clients
as well as email. If that wasn’t enough, it would download a file called
WIN-BUGFIX.EXE and execute it. This was not a bug fixing program but
rather a program that extracted user passwords and mailed them to the hacker.
The ILOVEYOU virus transmitted itself largely through email to contacts in infected computers, so your “secret admirer” message came from someone you knew and hence you were more likely to click on it. An earlier highly successful virus, Melissa, spread by offering a list of passwords for X-rated web sites. Email-based virus transmission is still a dominant mechanism. Sender headers and links are often disguised to make it look like the content is from a legitimate party.
Modern Exploits Targeting Microsoft Office
Microsoft Office documents remain a common initial infection vector for malware due to their widespread use and complex feature set. While macro-based attacks have long been a threat, modern exploits increasingly take advantage of other components within the Office ecosystem—many of which require little or no user interaction. Key techniques include:
- Social Engineering and Macros
- Office documents frequently use social engineering to trick users into enabling macros. Attackers embed malicious Visual Basic for Applications (VBA) code and accompany it with convincing instructions or warnings (e.g., “Enable content to view this document properly”). When macros are enabled, the malware is executed. Despite improved security defaults, macro-based attacks remain effective, especially when users are persuaded that the document is important or urgent.
- Embedded URLs in Documents
- Some Office-based attacks do not directly contain malware, but instead embed:
- Links to malicious websites that host malware or phishing pages.
- Credential harvesting pages, such as fake Microsoft 365 login screens.
- URLs that initiate the download of a second-stage payload when clicked.
- Because the file itself may be benign, this method is effective at bypassing static malware detection tools.
- Microsoft Equation Editor Exploit (CVE-2017–11882)
- This vulnerability exploits a stack buffer overflow in the legacy Microsoft Equation Editor component—a standalone executable embedded in Office for rendering equations. It has the advantage of not requiring macros of user interaction, allowing exploits to run automatically when the document is open. While the vulnerability has been patched, this attack is still widely effective because many users run older versions of Office where the Equation Editor is still present and unpatched.
- Follina Vulnerability – Microsoft Support Diagnostic Tool (CVE-2022–30190)
- The Follina exploit uses malicious documents to trigger the Microsoft Support Diagnostic Tool (MSDT) via a crafted URL embedded in an Office document. As with the equation editor exploit, there is no need for macros or explicit user permission. When the document is opened, MSDT is invoked using a specially crafted
ms-msdt:URL, which allows remote code execution, often launching PowerShell scripts to download and run malware. Because the vulnerability abuses a built-in Windows tool, traditional defenses such as macro blocking are ineffective.
To protect against these attacks:
- Keep Office and Windows fully updated.
- Disable macros from untrusted sources.
- Use endpoint protection capable of analyzing document behavior, not just contents.
- Block unusual protocol handlers (like
ms-msdt) where possible. - Educate users to be skeptical of unexpected attachments, even from familiar senders.
Malware Infiltration via JavaScript and PDF Files
JavaScript-Based Attacks
JavaScript, like Visual Basic, has evolved into a powerful, fully-featured programming language. It is embedded in nearly all websites and can dynamically manipulate web page content, respond to user interaction, and initiate asynchronous network requests.
While browsers have significantly improved in sandboxing and isolating web content, JavaScript remains a common attack surface due to its ubiquity and integration with other browser components. Malicious JavaScript can:
- Redirect users to phishing or exploit-laden websites,
- Harvest browser and system data (user agent, IP address, OS type),
- Scan internal networks, using the browser as a proxy to perform local IP port scans and report back findings,
- Exploit browser or plugin vulnerabilities, especially in older or unpatched systems.
JavaScript-based attacks are often embedded in malicious advertisements (malvertising) or exploit kits hosted on compromised websites. These scripts may deliver malware through drive-by downloads, requiring little or no user interaction beyond visiting a page.
Modern browsers implement content security policies, same-origin restrictions, and sandboxing, but attackers continue to find creative bypasses—particularly through browser extensions, third-party plugins, or unpatched vulnerabilities.
PDF-Based Attacks
As Microsoft Office began implementing stricter macro security, PDF files became a popular alternative for file-based malware delivery. PDFs are commonly perceived as static documents, but the PDF specification supports a range of dynamic features, including:
- Embedded JavaScript that executes on events (e.g., on open, on mouseover),
- Action triggers, such as automatically launching a URL or opening a file,
- Embedded files, including executables or scripts,
- Network requests, allowing the PDF to fetch live data from external servers.
These features enable attackers to craft seemingly harmless documents that execute malicious code when opened in vulnerable PDF readers. While modern PDF viewers display warnings when dynamic content is present, users may dismiss or ignore these messages, especially when accompanied by convincing social engineering.
Example attack: A phishing email includes an attached PDF labeled “Invoice_0425.pdf.” When opened, the file runs embedded JavaScript that redirects the user to a fake login page or downloads a second-stage payload.
Some malware authors also use PDF obfuscation techniques, such as hiding code in form fields, layering content streams, or encrypting sections, to evade static analysis.
Mitigations
To defend against JavaScript and PDF-based malware:
- Keep browsers, plugins, and PDF readers up to date,
- Disable JavaScript in PDF viewers unless explicitly required,
- Use viewer configurations that disallow automatic actions or embedded files,
- Rely on security software with behavioral analysis for document-based threats,
- Train users to treat unexpected or unsolicited documents with suspicion, even if they appear to come from trusted sources.
Trojan Horses
A Trojan Horse, or simply Trojan, is a type of malware that masquerades as legitimate or desirable software in order to deceive users into installing and executing it. It typically has two purposes:
- The overt purpose is the apparent, benign functionality that gives users a reason to trust the program, such as acting as a free utility, game, or productivity tool.
- The covert purpose is the hidden, malicious behavior embedded in the program, which operates without the user’s knowledge or consent.
Unlike viruses or worms, Trojans do not self-replicate or spread autonomously. Instead, they rely entirely on user interaction for delivery. Once executed, the Trojan may perform any number of malicious actions: stealing data, recording keystrokes, installing other malware, opening backdoors, or converting the system into part of a botnet.
A classic example of a Trojan involves command substitution in Unix-based systems. An attacker might place a script in a user’s search path with the same name as a common system command, such as ls. When the user invokes that command, the malicious script is run instead. The script may call the real ls command so the output looks normal, but in the background, it might create a setuid shell for later privilege escalation or quietly exfiltrate sensitive files. Because the expected behavior is preserved, the user may never notice anything suspicious.
Trojans are often found in pirated software or tools that claim to offer system enhancements or hacking utilities. In some cases, malicious actors embed Trojans in hacker tools, using the lure of offensive capabilities to target novice attackers: a form of “hackers hacking wannabe hackers.” In reality, these tools may activate webcams, log keystrokes, enroll the system in a botnet, or allow remote access by the attacker.
Example: Pinyin keyboard apps.
In April 2024, a report revealed that eight out of nine widely used Pinyin keyboard apps, designed for inputting Chinese characters, were vulnerable to keystroke interception. These apps were installed by roughly 76% of Chinese mobile users employing third-party keyboards. Whether these apps were deliberately malicious or simply poorly secured, the result was the same: they created opportunities for covert surveillance under the guise of providing useful functionality.
Remote Access Trojans (RAT)
Some Trojans are designed to serve as initial access tools, installing additional components such as rootkits or backdoors. Others are more specialized. A Remote Access Trojan (RAT) is a subtype that provides attackers with full control over a compromised system. Once a RAT is installed, it allows remote manipulation of files, observation of user activity, activation of hardware like microphones and webcams, and the download or execution of further malware. RATs are commonly used in targeted attacks and often include features to remain hidden for long periods.
Trojan horses continue to be an effective delivery mechanism for malware. Their success relies not on exploiting technical flaws in software, but on exploiting human trust.
Backdoors
A backdoor is software that is designed with some undocumented mechanism to allow someone who knows about it to be able to access the system or specific functions in a way that bypasses proper authentication mechanisms. In many cases, they are not designed for malicious use: they may allow a manufacturer to troubleshoot a device or a software author to push an update. However, if adversarial parties discover the presence of a backdoor, they can use it for malicious purposes. It is common for trojans to contain backdoors as part of the covert component.
An old, but classic, example of a backdoor is the sendmail mail delivery server. The author of sendmail wanted to have development access on a production system that had the program installed so that he can continue to improve it. The system administrator refused such access. His next release of sendmail contained a password-protected backdoor that gave him access to the system via the sendmail server. The password was hard-coded in the program and soon became well-known. Robert Morris used the knowledge of this backdoor as one of the mechanisms for his worm to propagate to other systems. More recently, in 2014, some Samsung Galaxy phones were delivered with backdoors that provide remote access to the data on the phone.
Example: the JAVS Viewer
As another example, let’s look at some of the basic deception techniques used in the JAVS Viewer. You’ve most likely never heard of this software, but it is used by courtrooms to record and play back audio and video from court proceedings. It is used in more than 10,000 courtrooms in the U.S. and 11 other countries.
In May of 2024, security researchers at Rapid7 reported that a version of the JAVS Viewer 8 available for download on the company’s website contained a backdoor that gives a threat actor access to devices that installed the software.
- The installer copied a binary file called
fffmpeg.exe. Note that ffmpeg is the name of a popular video decoder. On casual inspection, one might not notice the extrafin the name and assume it’s simply a legitimate video decoder. - The software was digitally signed but the certificate containing the public key was issued to a company called “Vanguard Tech Limited” and not the legitimate provider, which is “Justice AV Solutions Inc.”. Most users will just assume the software was signed by the legitimate publisher.
- When
fffmpeg.exeruns, it connects to a command-and-control server using Windows Sockets and WinHTTP. Using HTTP for communications will often not cause intrusion detection services to detect suspicious activity. The command-and-control server is the remote service that will allow the attacker to dispatch commands to the infected clients that connect to it. fffmpeg.exealso downloaded a file namedchrome_installer.exe. This also looks like a legitimate-sounding program, presumably one that downloads Google’s Chrome browser. In reality, it executes a binary program and several Python scripts that steal passwords saved in browsers.
You can read the full discussion here: Crooks plant backdoor in software used by courtrooms around the world.
Rootkits
A rootkit is software that is designed to allow an attacker to access a computer and hide the existence of the software … and sometimes hide the presence of the user on the system.
Historically, a basic rootkit would replace common administration commands (such as ps, ls, find, top, netstat, etc.) with commands that mimic their operation but hide the presence of intruding users, intruding processes, and intruding files. The idea is that a system administrator should be able to examine the system and believe that all is fine and the system is free of malware (or of unknown user accounts).
User mode rootkits
The rootkit just described is a user mode rootkit and involves replacing commands, intercepting messages, and patching commonly-used APIs that may divulge the presence of the malware. A skilled administrator may find unmodified commands or import software to detect the intruding software.
Kernel mode rootkits
A kernel mode rootkit is installed as a kernel module. Being in the kernel gives the rootkit unrestricted access to all system resources and the ability to patch kernel structures and system calls. For example, directory listings from the getdents64 system call may not report any names that match the malware. Commands and libraries can be replaced and not give any indication that malicious software is resident in the system.
Hypervisor rootkits
The most insidious rootkits are hypervisor rootkits. A hypervisor sits below the operating system and is responsible for translating between virtual device operations from operating systems and the underlying hardware. All I/O flows through the hypervisor. Most computer systems do not run virtual machines and hence have no hypervisor. These systems are prime targets for a hypervisor-based rootkit. Now you can have an environment where the entire operating system can run unmodified - or even be reinstalled - and be unaware that its operations are being intercepted at a lower level. The hypervisor does not have to virtualize all hardware interactions: just the ones it cares about. For example, it might want to grab keyboard events to record passwords and messages.
Hypervisor attacks have not been deployed but have been demonstrated as a proof of concept. The challenge in detecting their presence is that operating systems are unaware if they are running under a hypervisor, so if a malicious hypervisor is installed, the operating system needs to detect that it is running under a hypervisor rather than directly on the computer system. Detection is difficult and often relies on measuring completion times of certain system calls. If they go through a hypervisor, they will take a longer time and the on-chip Time Stamp Counter (TSC), which counts CPU cycles, will show a longer value with a hypervisor in place. An alternative, and far more obscure, method of detection, is the use of an instruction that stores the interrupt descriptor table register (IDTR) into a memory location (the SIDT instruction). The hypervisor changes the register’s value and the instruction can detect that. However, this does not have to take place on a system with only one operating system, so measuring timing differences may still be the more foolproof approach.
Ransomware
If we think back to the goals of malware, one common goal was to extract money: even hackers need to monetize their efforts. An indirect way of accomplishing this was by collecting information to gain access to bank account data, PayPal data, or modifying accounts that may take money, such as eBay accounts. A more direct way of getting money is to demand it from the victim. Ransomware is a relatively new form of malware that locks a computer, keeps it from booting, or encrypts all files on the system. It then asks the victim to pay a ransom (usually via bitcoin) to get a decryption program.
Gathering information
Malware has varying goals. These goals may include spying on user activity, destroying content, assembling a collection of servers, or extracting money from a victim. One common goal is to gather information … or get the user to provide information. Your computer might not have anything of direct value to an adversary, but your PayPal, bank, Amazon, or eBay credentials might be useful.
Phishing
Phishing is a social engineering attack whose most common purpose is to get personal information from someone, usually login credentials to some service. These are often carried out vie email with similar techniques that are used to spread infected files. A message announcing that your PayPal account is being canceled, that your bank detected a fraudulent transaction, or that FedEx could not deliver a package may prompt the receiver to panic and immediately click on a link in the message, which may result in the browser displaying a site crafted to look like PayPal, the bank, or FedEx and prompt the user for login and password information.
A 2023 OpenText Cybersecurity Threat Report identifies email phishing as the primary vector for infection (followed by accessing Microsoft’s Remote Desktop Protocol, RDP).
Phishing attacks are surprisingly effective. A 2018 study by Proofpoint found that 52% of all successful phishing emails are clicked on within one hour of being sent.
A 2017 report by Webroot found that 1.385 million new and unique phishing sites are created each month. Their 2019 report pointed out that phishing attacks increased 36 percent over 2018 and the number of phishing sites grew over 220 percent.
Spear phishing
Spear phishing is a targeted and highly deceptive form of phishing. While traditional phishing casts a wide net, sending the same deceptive message to many recipients in the hope that a few will be tricked, spear phishing focuses on a specific individual or organization. These attacks employ highly customized messages that demonstrate knowledge of the target, making them appear legitimate and increasing their likelihood of success.
One well-known example is the 2016 Democratic National Committee (DNC) breach, which was facilitated through spear phishing. Attackers sent emails containing bit.ly links—URL shorteners that masked the true destination. Clicking the link redirected users to a fake Google login page, pre-filled with their actual email address. Thinking the page was legitimate, users entered their passwords, inadvertently handing over their credentials to attackers.
More recent Gmail spear phishing campaigns follow a similar approach but have become even more deceptive. Attackers hijack compromised accounts and send phishing emails to the victim’s contacts. These emails include an attachment that appears to be a document preview—often an actual file from the victim’s email history to enhance credibility. Clicking the attachment leads to a phishing page designed to steal login credentials. Once attackers gain access, they repeat the cycle, expanding their network of compromised accounts.
** The role of generative AI and data breaches in advanced spear phishing **
Spear phishing attacks have become easier to automate, more cost-effective, and increasingly difficult to detect, largely due to the convergence of generative AI and the mass availability of personal data from large-scale breaches. Generative AI tools can dynamically generate phishing emails that are indistinguishable from legitimate business communication, incorporating contextually relevant details that make the deception nearly flawless.
Massive data breaches over the past decade have exposed billions of email addresses, passwords, social media interactions, and behavioral data. Attackers can now feed this information into AI models to generate personalized phishing emails that reference real-life details—such as the target’s job role, recent purchases, or social connections—making these scams far more believable. This level of personalization eliminates the red flags that traditionally help users identify phishing attempts.
AI-driven spear phishing campaigns are not only more convincing but also cheaper and more scalable. Attackers can now automate:
- Hyper-personalized phishing emails, customized for each recipient
- Context-aware responses, making phishing conversations feel more natural
- Social engineering scripts, tailored for calls, messages, or interactive phishing sites
- Deepfake-enhanced attacks, where AI-generated voice or video adds credibility
This shift has already been observed in large-scale spear phishing operations, such as the North Korean “DeceptiveDevelopment” campaign. In 2025, cybersecurity researchers uncovered this job interview-themed spear phishing attack, in which North Korean hackers posed as recruiters on job-hunting sites like Upwork and Freelancer.com. Attackers lured freelance developers with fake job offers, sharing trojanized software projects via platforms like GitHub and GitLab that installed backdoor malware when executed.
Another variant of the attack involved malicious video conferencing software, which shows how spear phishing is evolving beyond email into other professional platforms.
These attacks, part of a broader strategy by North Korea to steal cryptocurrency and sensitive credentials, show how spear phishing campaigns can exploit professional and career-oriented platforms to gain trust. Unlike generic phishing scams, which rely on generic scare tactics, these attacks are deeply researched, highly personalized, and executed with strategic precision.
According to the 2023 OpenText Cybersecurity Threat Report, spear phishing now accounts for 8.3% of all email traffic. Attackers increasingly leverage generative AI to craft highly convincing emails, mimicking legitimate communication with fewer detectable flaws. This, combined with the vast amount of compromised personal data available through breaches and leaks, allows adversaries to create remarkably convincing phishing messages. As a result, large-scale spear phishing campaigns can now target individuals with an unprecedented level of customization, making them significantly harder to detect.
As spear phishing attacks evolve, defense strategies must also advance. Employees and individuals should remain cautious of unexpected emails, verify senders independently, and use multi-factor authentication to mitigate risk. Cybersecurity awareness, proactive monitoring, and robust security protocols remain the best defense against these increasingly sophisticated threats.
Phishing warning signs
Some warning signs that a mail message may be a phishing attack are:
From header: is it from an unknown or suspicious address?
To header: if the message is sent to multiple people, do you recognize any other names on the header?
Date header: if the message purports to be a personal message, was it sent during normal business hours?
Subject header: is the suspicious and is it relevant to your activities?
Message content: is the message a request to click on a link in order to avoid a negative consequence?
Embedded links: are there any links that you are asked to click? If you look at the target of those links, are they misspelled, suspicious, or for a site different from that of the sender?
Attachments: is there an unexpected attachment that you are expected to open, such as a Microsoft Word document or PDF file?
Smishing attacks
Smishing, short for “SMS phishing,” is a specific type of social engineering attack that exploits trust and urgency to deceive individuals into revealing sensitive information, installing malicious software, or taking harmful actions. Like phishing emails, smishing leverages psychological manipulation, but instead of email, it uses SMS text messages or messaging apps as the delivery medium. The ubiquity of mobile devices makes smishing particularly effective, as people often perceive text messages as more personal and urgent than emails.
Smishing attacks typically include messages that impersonate a trusted entity, such as a bank, delivery services (USPS, UPS, FedEx, DHL, etc.), government agency, e-commerce platform, or even a personal contact. These messages often contain a sense of urgency, like warnings about account suspensions, delivery problems, fraudulent activity, or missed payments.
A smishing message may include a link to a malicious website that mimics a legitimate one or a phone number that connects the victim to an attacker posing as customer support. In other cases, the message may prompt the recipient to reply with sensitive information, such as login credentials, credit card numbers, or one-time verification codes.
The rise of smishing is tied to the widespread use of smartphones, which blur the lines between personal and professional communication. Many users are less cautious when interacting with text messages compared to email, making them easier targets. Additionally, the increasing use of SMS for multi-factor authentication (MFA) has made smishing attacks more lucrative, as attackers attempt to intercept codes and gain unauthorized access to accounts.
Example: Increased sophistication
In recent smishing attacks, attackers have devised a method to bypass Apple’s iMessage security features by manipulating users into disabling built-in protections.
iMessage includes a “Filter Unknown Senders” feature that automatically disables links in messages from unknown contacts, preventing users from inadvertently clicking on potentially malicious URLs. However, attackers have been sending deceptive messages prompting recipients to reply with “Y” or similar responses.
When a user replies or adds the sender to their contacts, iMessage considers the sender trusted and re-enables the previously disabled links. This tactic exploits user trust and familiarity with responses to automated services, with messages like “STOP” to unsubscribe or “Yes” or “No”.
Once a user responds, links become activated, and users may click on them, leading to phishing sites designed to steal personal information or install malware.
See Phishing texts trick Apple iMessage users into disabling protection, Bleeping Computer, January 12, 2025.
Voice phishing
The huge shift to work-at-home environments in 2020 due to the covid pandemic led to attackers trying to get access credentials to corporate networks from employees working from home. One technique that was created was voice phishing.
A vishing (voice phishing) attack involves an attacker contacting employees at home and using pretexting to convince them that they are calling from the company’s IT department to troubleshoot connectivity problems on the corporate VPN. The attacker may create plausible-looking LinkedIn profiles to help in this deception.
In its simplest form, the attacker may simply obtain access credentials via the voice call. To improve the odds of success, attackers have created phishing pages that look like they belong to many of the world’s biggest companies. These pages request login credentials, including one-time passwords or any special access codes required by the company. When an victim enters data in that page, the attacker can immediately log into the corporate network.
Example: Increased sophistication
A January 2025 article by Brian Krebs, A Day in the Life of a Prolific Voice Phishing Crew details the operation of a voice phishing gang that blends technological manipulation with psychological tactics to exploit user trust.
The voice phishing attack described in the article involves a highly coordinated effort to exploit trust and abuse legitimate services. The attackers, organized into specific roles such as caller, operator, drainer, and owner, manipulate their targets through a combination of spoofed calls and social engineering.
The process begins by bombarding the target’s devices with fake account recovery notifications, leveraging services like Apple’s automated phone support system to make the alerts appear genuine. By spoofing a legitimate Apple phone number, the attacker gains credibility when contacting the victim. The caller, pretending to be from Apple support, convinces the victim to engage further, offering reassuring, scripted responses.
The critical step in the attack involves directing the victim to a phishing website designed to mimic Apple’s login page. Once the victim enters their credentials, the operator silently captures this data and uses it to access the victim’s accounts, often to steal cryptocurrency or sensitive data. Throughout the attack, the attackers maintain the victim’s trust by mirroring legitimate support interactions, making the victim feel they are securely resolving an account issue.
Embedded URLs
Astute users who are aware of phishing attacks have become accustomed to examining the targets of a link rather than just blindly clicking on a link (unfortunately, this may not be possible on mobile devices in many cases). If the link looks suspicious, the likelihood of it being clicked diminished. In addition to setting up misspelled and authentic-sounding domain names, attackers found it convenient to simply use URL shortening services, such as bit.ly. For example, a link to poopybrain.com may appear suspicious but a link to https://bit.ly/30zQv0u disguises the target and users are accustomed to receiving shortened URLs for legitimate content.
Mail servers, such as Microsoft’s Office 365 service, build up lists of known malicious links and attackers need to get through those systems. They recently realized that they could get around filtering services by using IP addresses instead of domain names in URLs. On top of that, the IP address need not be presented in the standard dotted-decimal notation but may be in octal or hexadecimal as well as non-dotted formats. All of the following addresses are equivalent:
| http://www.poopybrain.com |
| http://73.215.234.231 |
| http://0111.0327.0352.0347 |
| http://0x49.0xd7.0xea.0xe7 |
| http://0x49D7EAE7 |
| http://011165765347 |
| http://1238887143 |
Calendar injection
A social engineering attack that has gained popularity in 2020 and the expanded use of video conferencing is calendar injection.
An attacker inserts a calendar event into the victim’s calendar. The event is a plausible-sounding video conference (think of topics such as staff meeting, all-hands meeting, company update, performance review, or corporate restructuring and workforce adjustment). When the victim clicks on the link, the browser may present a dialog box asking the user for permission to “open” the program needed to run the conference … or to download the conference program. These are expected events in normal conferences. In reality, of course, the link or the downloaded program will be malicious.
Attackers can install these injections via various forms of malware or via a malicious website that would download a calendar invitation. More commonly, the calendar event can be sent in a spoofed mail message and the mail client software may automatically parse the message, see the invitation, and add it to the calendar.
Deceptive websites
Malicious links in phishing attacks often direct the user to a website in order to obtain their login credentials. These sites masquerade as legitimate sites. The Proofpoint study mentioned earlier found that for every legitimate website, there are 20 malicious sites that mimic it. Attackers register domain names that closely resemble legitimate ones, often exploiting common typing errors (e.g., “gooogle.com” instead of “google.com”), to deceive users into thinking they are visiting legitimate sites. This is known as typosquatting. Such sites can be masqueraded banking sites, Google/Microsoft/Apple authentication pages, videoconferencing plugin-software downloads, etc.
Combosquatting is a technique where attackers register domain names that combine a legitimate brand or keyword with additional terms or characters to create deceptive URLs, tricking users into thinking the site is authentic (e.g., “secure-bank-login.com” instead of “bank.com”).
Even if a site isn’t malicious, it may have links to or have embedded malicious content. File serving sites, including those that host software or those that provide services such as PDF, video, or audio conversion services are often ad-sponsored. Some of the ads on these sites are often disguised to look like download links and can trick a user into clicking on the ad instead of the link for the actual content the user wants.
Deceptive pop-ups are another malicious tactic used by attackers to trick users into executing harmful actions, often by mimicking legitimate system or browser error messages. In one attack campaign, attackers use fake Google Chrome error pop-ups claiming a critical update is needed, urging users to download and run a malicious file. This file executes a PowerShell script to deploy malware, leveraging the user’s trust in familiar interfaces and urgency to bypass security awareness.
All of these attacks rely on social engineering to compromise systems without exploiting technical vulnerabilities.
Keyloggers
Another way of obtaining information is to snoop on a user’s actions. Keyloggers record everything a victim types and allow a user to extract login names, passwords, and entire messages.
Keyloggers can be implemented in several ways:
- Malicious hypervisor
- Since a hypervisor provides virtual interfaces for all the resources of a computer, it can capture all keyboard, mouse, and even video data. These attacks are difficult since they rely on the ability to install a hypervisor.
- Kernel-based rootkit
- All input/output operations go through the operating system kernel. Modifying the kernel allows malicious software to log and upload keystroke data.
- System call hooking
- Some operating systems provide a system call hooking mechanism that allows
data to and from system calls to be intercepted. We saw how this was used to
implement sandboxing. Windows enables this without
having to install any kernel-level drivers. The
SetWindowsHookExsystem call can be used to report WH_KEYBOARD and WH_MOUSE events, capturing keyboard and mouse activity. - Browser-based logging
- JavaScript can be used to capture
onKeyUp()events. These events will be captured for one page but other hacks can be used to create a broader context with embedded pages. Form submission can also be intercepted to get populated form data without having to reassemble key presses into coherent account credentials. - Hardware loggers
- Although visible to the user, hardware key loggers can be used for USB-connected keyboards. Some of these have embedded Wi-Fi transceivers that enable an attacker to collect the data from a distance.
File-less malware
File-less malware is a type of malicious software that operates entirely in memory, avoiding the creation or storage of traditional files on disk, which makes it difficult to detect using conventional antivirus tools. Instead of leaving a recognizable footprint on the system, file-less malware exploits legitimate system tools and processes, such as PowerShell, WMI (Windows Management Instrumentation), or registry keys, to execute its payload.
This stealthy approach enables attackers to bypass traditional defenses like signature-based detection. File-less malware is particularly dangerous because it leaves little forensic evidence, is harder to detect and analyze, and can often exploit vulnerabilities in trusted software or system configurations. Its ability to operate undetected for extended periods makes it a potent weapon for cybercriminals conducting espionage, data theft, or targeted attacks.
Defenses
Malware was particularly easy to spread on older Windows systems since user accounts, and hence processes, ran with full administrative rights, which made it easy to modify any files on the system and even install kernel drivers. Adding file protection mechanisms, such as a distinction between user and administrator accounts added a significant layer of protection. However, malware installed by the user would run with that user’s privileges and would have full access to all of a user’s files. If any files are read or write-protected, the malware can change DAC permissions.
Systems took the approach of warning users if software wanted to install software or asked for elevated privileges. Social engineering hopes to convince users that they actually want to install the software (or view the document). They will happily grant permissions and install the malware. MAC permissions can stop some viruses as they will not be able, for instance, to override write permissions on executable files but macro viruses and the user files are still a problem.
In general, however, studies have shown that by simply taking away admin rights (avoiding privilege escalation) from users, 94% of the 530 Microsoft vulnerabilities that were reported in 2016 could be mitigated and 100% of vulnerabilities in Office 2016 could be mitigated.
Email authentication
Since fraudulent email is such common attack vector, three mechanisms have been created to address this. SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) work together to authenticate email senders and prevent malicious activities like phishing and email spoofing.
SPF allows domain owners to specify which mail servers are authorized to send emails on their behalf. This information is published in the domain’s DNS TXT record, and recipient servers check the SPF record to verify whether the sending server’s IP is authorized. Emails from unauthorized servers may be flagged as spam or rejected.
DKIM ensures the integrity of an email by adding a digital signature to the email header, which is created using the sender’s private key. The recipient’s server uses the public key, published in the sender’s DNS records, to verify the signature. If the signature is valid, it confirms that the email has not been altered during transmission and that it originated from the claimed domain.
DMARC builds on SPF and DKIM by providing instructions to receiving servers on how to handle emails that fail these checks. Domain owners define a DMARC policy in their DNS records, specifying whether emails failing SPF or DKIM checks should be quarantined, rejected, or allowed. DMARC also enables domain owners to receive reports about authentication failures, helping them monitor and secure their email ecosystem.
The DKIM Replay Attack
A 2025 attack campaign shows how attackers sent emails that appear to come from Google’s infrastructure and pass the DKIM signature check. This is called a DKIM Replay Attack and it enabled the attackers to send convincing phishing messages that appear to have been created by Google.
A DKIM Replay Attack leverages the trust built into DKIM (DomainKeys Identified Mail) by resending a message that was originally signed by a legitimate domain, such as Google, without modifying its content. Because the signature remains valid, the message will continue to pass authentication checks even when forwarded to others. This attack is particularly dangerous because DKIM-signed messages are generally considered trustworthy by email providers and recipients.
In the documented case, the attacker begins by creating a Google account that they control. They then set up a fake OAuth application. An OAuth application is any app that requests access to a user’s account via the OAuth protocol, commonly used to allow apps to request limited permissions (like reading your email or accessing your profile) without needing your password. When the attacker connects their fake OAuth app to their own Google account, Google generates and sends a security alert email to that account, warning that a new app has been granted access.
Because this email is automatically generated by Google and sent from a legitimate domain, it is DKIM-signed and fully authentic. The attacker now has a clean, signed message that appears to be a legitimate Google security alert. Without altering it, they forward this email to victims using third-party infrastructure such as custom SMTP relays or mail-forwarding services. Because the DKIM signature is still intact, the message appears genuine and passes all authentication checks (SPF, DKIM, and DMARC).
The email typically contains a link to a phishing site hosted on a trusted subdomain like sites.google.com. This page mimics the real Google Support or login interface but is controlled by the attacker. Victims who click the link are prompted to enter their credentials, which are then harvested. Because all email authentication checks pass and the message seems to come directly from Google, most recipients have no reason to suspect a phishing attempt.
This attack cleverly exploits a blind spot in DKIM: once a message is signed, its authenticity can’t be revoked or expired. The use of OAuth in this case doesn’t involve breaking OAuth itself—instead, it’s a way to get Google to legitimately sign and send an email the attacker can later “replay” to other users. This highlights how trust in authentication mechanisms can be abused when attackers manipulate legitimate systems for malicious purposes.
Steps in the DKIM Replay Attack
Create a Google Account The attacker sets up a new Google account they control (e.g.,
me@attacker-domain.com).Register a Fake OAuth Application The attacker creates an OAuth app under the same Google account. This app may have a misleading name (e.g., “Security Alert”) to match the content of the phishing message.
Grant OAuth Access The attacker authorizes their fake OAuth app to access their own Google account, triggering a legitimate security alert email from Google.
Receive a DKIM-Signed Email Google sends a real security alert to the attacker’s inbox, signed with a valid DKIM signature from
accounts.google.com.Forward the Email Unmodified The attacker forwards the same signed email to victims using a third-party SMTP service or forwarding infrastructure, keeping the DKIM signature intact.
Victim Receives Trusted-Looking Email The victim’s email system accepts the email because it passes SPF, DKIM, and DMARC checks, making it appear legitimate.
Email Contains a Phishing Link The email includes a link to a phishing page hosted on
sites.google.com, which looks like a real Google login or support page.Credential Theft The victim clicks the link and unknowingly enters their credentials on the fake page, which are then captured by the attacker.
Anti-virus (anti-malware) software
There is no way to recognize all possible viruses. Anti-virus software uses two strategies: signature-based and behavior-based approaches.
With signature-based systems, anti-virus programs look for byte sequences that match those in known malware. Each bit pattern is an excerpt of code from a known virus and is called a signature. A virus signature is simply a set of bytes that make up a portion of the virus and allow scanning software to see whether that virus is embedded in a file. The hope is that the signature is long enough and unique enough that the byte pattern will not occur in legitimate programs. This scanning process is called signature scanning. Lists of signatures (“virus definitions”) have to be updated by the anti-virus software vendor as new viruses are discovered. Signature-based detection is used by most anti-virus products.
With Heuristic analysis, the system monitors the activities of a process (typically the system calls or standard library calls that it makes). This is a behavior-based technique.
With static heuristic analysis, the potentially malicious code is not run but is decompiled to source code. The source code is compared with source code in a database of known malicious code. The analyzer looks for suspicious operations, such as attempts to access specific files, certain system calls, use of packers, attempts to create self-modifying code. Each of these can increase the “score” of the item being scanned. If the score is high enough, it can be market as suspicious.
With dynamic heuristic analysis, the code is executed. Some form of isolation is required. Sandboxing is usually employed, to ensure that the suspected code is run within a sandbox or even in an interpreted environment within a sandbox to ensure that it cannot cause real damage. Behavior-based systems try to perform anomaly detection. If the observed activity is deemed suspicious, the process is terminated and the user alerted. Sandboxed, behavior-based analysis is often run by anti-malware companies to examine what a piece of suspected malware is actually doing and whether it should be considered to be a virus. A behavior-based can identify previously-unseen malware but these systems tend to have higher false positive rates of detection: it is difficult to characterize exactly what set of operations constitute suspicious behavior.
Windows Defender, as an example, makes use of both signature-based scanning, static heuristic analysis, as well as dynamic process monitoring. It uses signature-based scanning on files and behavior-based analysis for running processes. Behavior monitoring includes scanning for suspicious file and registry changes (e.g., ransomware may try to encrypt all the files on a system and a lot of malware may try to modify the registry so that the software runs when the system is rebooted.
Countermeasures used by attackers
Some viruses will take measures to try to defend themselves from anti-virus software.
Signature scanning countermeasures
A common malware tactic is to use a packer on the malicious payload, unpacking it prior to execution. Packers play a crucial role in malware evasion techniques. A packer is a type of software used to compress and/or encrypt the malicious code in a file to change a virus’s signature.
Packing can done in several ways:
- Compress the code and then uncompress it upon loading it prior to execution. One can scan for a signature of a compressed version of the virus, but there are dozens of compression algorithms around, so the scanning process becomes more complicated.
- Simply obscure the malware payload by exclusive-oring (xor) with a repeating byte pattern (exclusive-oring the data with the same byte pattern reconstructs it. This is a simple version of a stream cipher.
- Encrypt the code and decrypt it prior to execution.
With encryption (xor is a simple form of encryption), only the non-encrypted part of the virus contains the unpacking software (decryption software and the key). A virus scanner will need to match the code for the unpacker component since the key and the encrypted components can change each time the virus propagates itself.
Polymorphic viruses mutate their code each time they run while keeping the algorithm the same. This involves replacing sequences of instructions with functionally-identical ones. For example, one can change additions to subtractions of negative numbers, invert conditional tests and branches, and insert or remove no-op instructions. This thwarts signature scanning software because the byte pattern of the virus is different each time.
Defending with access controls and sandboxing
Access controls help but do not stop the problem of malware. Containment mechanisms such as containers work well for server software but are usually impractical for user software (e.g., you want Microsoft Word to be able to read documents anywhere in a user’s directories). Application sandboxing is generally far more effective and is a dominant technique used in mobile software.
Trojans, deceptive downloads, and phishing attacks are insidiously difficult to defend against since we are dealing with human nature: users want to install the software or provide the data. They are conditioned to accepting pop-up messages and entering a password. Better detection in browsers & mail clients against suspicious content or URLs helps. However, malware distributors have been known to simply ask a user to rename a file to turn it into one that is recognized by the operating system as an executable file (or a disk image, PDF, or whatever format the malware come in and may otherwise be filtered by the mail server or web browser.
Countermeasures against sandboxed environments
Viruses are unlikely to get through a sandbox (unless there are vulnerabilities or an improper configuration). However, there are areas where malware can address sandboxing:
Vendor examination
Anti-virus vendors often test software within a tightly configured sandboxed environment so they can detect whether the software is doing anything malicious (e.g., accessing files, devices, or the network in ways it is not supposed to). If they detect that they do have malware, they will dig in further and extract a signature so they can update and distribute their list of virus definitions. Viruses can try to get through this examination phase by setting a trigger to keep the virus from immediately performing malicious actions or to stay dormant for the first several invocations. The hope is that the anti-virus vendors will not see anything suspicious and the virus will never be flagged as such by their software.User configuration (entitlements)
Virtually all mobile applications, and increasingly more desktop/laptop applications, are run with application sandboxes in place. These may disallow malware from accessing files, devices, or the network. However, it never hurts to ask. The software can simply ask the user to modify the sandbox settings. If social engineering is successful, the user may not even be suspicious and not wonder why a game wants access to contacts or location information.
Modern Techniques for Deploying Stealthy Malware
As malware continues to evolve, attackers have adopted increasingly sophisticated techniques to avoid detection, maintain persistence, and infiltrate systems without raising red flags. Traditional signature-based and heuristic detection methods are often insufficient against these new methods. This list outlines some modern stealth techniques employed by malware authors.
Call Stack Spoofing
Call stack spoofing is a technique in which malware manipulates the stack frames to hide the origin of function calls. This obscures the execution path, making it difficult for analysts and automated tools to trace how a suspicious API or system call was initiated. Malware like Hijack Loader and CoffeeLoader use fabricated EBP chains to make malicious calls appear as if they originated from legitimate software modules.
Code-Signing Certificate Abuse
In this method, malware authors sign their payloads using stolen or fraudulently obtained code-signing certificates. This exploits the trust model used by many operating systems and antivirus programs, which often treat signed code as safe. Hijack Loader has been distributed using valid certificates, making it more difficult to flag as suspicious, even though the behavior remains malicious.
Use of Obscure Programming Languages
By writing malware in languages such as Rust, Delphi, Haskell, Lisp, or Go, attackers complicate the work of reverse engineers and evade many static analysis tools. These languages can produce binaries with unusual memory layouts, fragmented shellcode, and complex execution models that aren’t well supported by traditional malware detection tools. Groups like APT29 and ransomware families like Hive and Akira have adopted this approach.
DLL Side-Loading
This technique involves placing a malicious DLL with the same name as a legitimate one in a location where a vulnerable application will load it. The attacker uses a legitimate signed executable to trigger the loading of the malicious DLL. Malware like VARGEIT and SHELBYLOADER use this method to execute in the context of trusted processes, often with elevated privileges.
Abuse of GitHub and Other Cloud Services
Some malware communicates with command-and-control (C2) servers by abusing legitimate cloud services like GitHub, OneDrive, or Pastebin. For example, SHELBYLOADER uses GitHub repositories to exchange encrypted data and commands. This technique blends malicious traffic with benign cloud activity, reducing the likelihood of detection by network monitoring tools.
Anti-VM and Anti-Debugging Checks
To avoid detection in sandbox environments, malware includes checks to detect whether it’s running in a virtual machine or being debugged. If such conditions are detected, the malware halts execution or behaves benignly. Hijack Loader includes modules like ANTIVM, while others delay execution or look for signs of analysis software.
Timestomping
Timestomping involves altering the file timestamps of malicious artifacts to make them appear older or to match system files. This evasion technique is used to defeat forensic analysis and blend the malware into the system environment. Earth Alux uses a module named RAILSETTER specifically for this purpose.
Fileless Malware
Fileless malware executes entirely in memory without writing payloads to disk, making it difficult for antivirus software to detect. These attacks often use PowerShell or other scripting engines to download and execute payloads directly in RAM. SHELBYLOADER and some versions of Hijack Loader employ this tactic.
Living Off the Land (LotL)
This approach uses legitimate system utilities like PowerShell, WMI, mshta.exe, and regsvr32.exe to execute malicious code. Because these tools are built into Windows and commonly used by administrators, their abuse often goes unnoticed. Hijack Loader, for example, uses mshta.exe to execute code hosted on a remote server.
Encrypted and Obfuscated Network Communication
Malware frequently encrypts its network traffic to prevent inspection. This may involve standard protocols like HTTPS or custom encryption schemes. Earth Alux’s VARGEIT tool communicates using multiple protocols (HTTP, DNS, Outlook Graph API) and encrypts messages to conceal the content of C2 communications.
Process Injection and Hollowing
Malicious code is injected into the memory space of a legitimate process, such as Notepad or RegSvcs. In process hollowing, the legitimate code is removed and replaced with the malicious payload. This technique allows the malware to run under the guise of a trusted application, complicating detection.
Steganography and Non-Executable Embedding
Attackers hide payloads in non-executable files like images or document metadata. For example, the GHOSTPULSE variant of Hijack Loader hides data within the pixel structure of PNG images. This approach bypasses content filters and static detection mechanisms.
GPU-Based Execution
Some malware offloads parts of its execution to the GPU, which typically lacks the same level of scrutiny as the CPU by security tools. This allows the malware to operate in parallel with the CPU and evade user-mode detection. CoffeeLoader is one such example that is exploiting this technique.
Modular and Delayed Activation
To avoid early detection, malware is often modular and activates its components only under certain conditions, such as specific times, user actions, or geographic locations. Some malware includes checks for the presence of specific antivirus processes before proceeding. This delay allows them to evade time-limited sandbox analysis.
Use of Standard APIs and Services for C2
Malware like Earth Alux’s VARGEIT uses standard services such as Microsoft Outlook’s Graph API to communicate with C2 servers. By embedding commands in email drafts and communicating through normal service channels, the malware avoids triggering typical network alerts.
These newer techniques reflect malware developers' evolving sophistication. Defensive strategies will have to evolve accordingly, focusing on behavioral detection, threat intelligence (which involves collecting and analyzing data about emerging threats and attacker behaviors), and memory-level analysis to catch these stealthy threats.
Honeypots
Honeypots are decoy systems, applications, or data set up to gather information about attackers and their methods. They are designed to mimic real systems that attackers might target, but they’re isolated and monitored environments. Some ways that honeypots are used are:
- Detection
- Honeypots can detect malicious activity by monitoring for interactions that should only occur if an entity is attempting to probe, attack, or compromise a system. Diversion
- By engaging attackers with fake systems, honeypots can divert their attention from real targets, potentially preventing actual breaches. Information Gathering
- Since honeypots are designed to be attacked, they provide a valuable source of information about how attackers operate, including the tools they use, the vulnerabilities they exploit, and the types of data they seek. Research
- Researchers use honeypots to study the behavior of cyber threats in a controlled environment. This research can lead to better defenses and understanding of cybercriminal tactics. Improving Security Response
- The insights gained from honeypot interactions can help organizations improve their security posture. This includes refining security policies, patching vulnerabilities, and enhancing detection capabilities. Training
- Honeypots offer a real-world environment for cybersecurity professionals to train in detecting and responding to threats without the risk of damage to the actual network.
There are various types of honeypots, ranging from low-interaction honeypots, which simulate only the services frequently scanned by attackers, to high-interaction honeypots, which are complex and fully-functional systems designed to engage attackers more deeply. The choice between them depends on the specific goals, such as whether the focus is on gathering intelligence or on diverting attackers from more valuable assets.
References
2022 BrightCloud® Threat Report, BrightCoud Threat Intelligence.
Fedor Sinitsyn, Petya: the two-in-one trojan, SecureList, May 4, 2016
hasherezade, Petya – Taking Ransomware To The Low Level, Malwarebytes Labs, April 1, 2016
Don’t Panic, But All USB Devices Have a Massive Security Problem, How-To Geek, 2014.
Hackers Exploit Legitimate Packer Software to Spread Malware Undetected, The Hacker News, June 6, 2024.
Lavasoft, LNK Exploits, 2010
IEEE Spectrum, The Real Story of Stuxnet, February 2013.
Trend Micro SimplySecurity, Macro Malware: Here’s what you need to know in 2016, March 2016
SANS, PDF Malware Overview, July 2010.
George Ou, Blue Pill: The first effective Hypervisor Rootkit, ZDNet, August 15, 2006
DataBreachToday. “Malicious Python Package Exfiltrates AWS Credentials”
SentinelOne. “Exploiting Repos: 6 Ways Threat Actors Abuse GitHub & Other DevOps Platforms”
-
Matthew Tischer, Zakir Durumeric, et al., Users Really Do Plug in USB Drives They Find, University of Illinois, ↩︎